什么是勒索软件?
Ransomware is nefarious code or actions attackers deploy to disrupt an organization’s operations, 通常是用他们的数据作为人质. The ultimate goal is to force a business to pay a ransom so it can return to st和ard operations.
它是 nearly impossible to harden defenses to the point where an organization is completely impenetrable to ransomware attacks. 它是, 然而, possible to dramatically improve the ability to mitigate the worst effects of an attack or reduce the odds of being attacked in the first place.
勒索软件的类型
试图列出勒索软件的类型可能会变成一场追逐游戏. 事实上,美国网络安全和基础设施安全局(CISA) 调用ransomware 一种“不断进化的恶意软件”.“一些比较常见的勒索软件变种包括:
- 双勒索: Attackers will collect a first ransom 和 then threaten to sell the stolen data unless a second payment is made.
- Ransomware-as-a-Service(老城): Established ransomware syndicates sell easy-to-deploy ransomware "kits" so that even non-experts can launch sophisticated attacks.
- 分布式拒绝服务:而不是一个系统针对另一个系统, this type of attack involves many systems – hundreds or thous和s – launching a coordinated attack against one system.
- 鱼叉式网络钓鱼:攻击者精心制作, targeted email messages to a specific recipient or group in the hopes of fooling a target into clicking or downloading a malicious payload or initiating an undesired action such as a wire transfer.
- 偷来的凭证: Attackers use a set of stolen credentials taken from a compromised endpoint to gain access to subsequent targeted systems on the same network, 可能会锁定所有其他访问这些系统的权限.
- 应用程序开发: Attackers exploit vulnerabilities in an application to gain access 和 steal data 和/or deny service.
勒索软件是如何工作的?
勒索软件的工作原理是试图强迫受害者支付赎金. 具体来说, 恶意软件 由攻击者在勒索软件攻击中部署将遵循闯入模式, 恶意加密目标数据, 然后强迫公司或个人支付赎金.
如上所述,双重勒索已经变得越来越普遍. 对于现代攻击者来说,阻止对公司数据的访问是不够的, 他们也看到了偷窃的价值,并要求额外的报酬来取回它.
勒索软件对网络系统的影响各不相同, 取决于防御的类型和反应时间. 当获得访问权限时, attackers can use post-exploitation frameworks to search the environment 和 gain elevated privileges. 如果威胁行为者获得了完全的访问权限, 他们可以加密整个网络, 导致业务服务完全中断.
Infected endpoints in the larger network ecosystem could contain the threat for a period of time, 但在恶意软件传播之前,这是一场与时间的赛跑. Rapidly removing these infected assets is essential to limiting the blast radius of an attack.
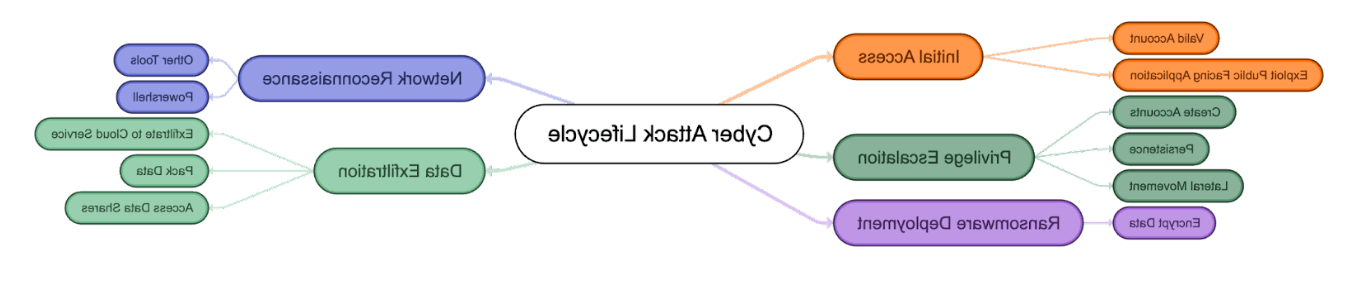
勒索软件攻击的各个阶段
- 初始访问和持久化: The first stage of the ransomware attack chain involves gaining access to an organization's network. 攻击者利用的常见技术包括网络钓鱼, 凭据填料, 漏洞利用.
- 侦察在这个阶段, 攻击者绘制出组织的网络, where they'll work to gain initial context around the systems 和 user privileges they have obtained. 对于攻击者来说,这通常是最复杂的阶段.
- 证书盗窃和横向移动:在进入组织的网络后, the attacker will attempt to obtain administrative credentials so they can move freely around the network. 在此期间,攻击者可能会禁用现有的任何安全协议.
- 漏出在此阶段,攻击者正在寻找从网络中泄漏的文件. 这些敏感文件将被用来勒索. 例子包括财务文件, 会计信息, 客户端数据, 项目信息, 和更多的.
- 加密最后一个阶段是加密——这通常是对组织影响最大的阶段. The attacker encrypts various target files, subsequently dem和ing a ransom for their return.
Ransomware例子
勒索软件在当今世界无处不在. 让我们来看看最近一些值得注意的例子.
WannaCry Ransomware
这2017 WannaCry勒索软件攻击 是最近最著名和最臭名昭著的勒索软件之一吗. It deviated from traditional ransomware by including a component that was able to find vulnerable systems 和 spread quickly. 因为这种行为, 这种类型的勒索软件被称为蠕虫, 在网络中挖隧道,造成最大的破坏.
Due to the nature of employing both traditional phishing tactics 和 the worm format of the 恶意软件, 这一事件尤其恶劣,并在全球范围内造成了影响. A Bitcoin ransom was dem和ed from users as well as organizations who typically did not have up-to-date software 和/or potentially poor hygiene around permissions, 密码, 和凭证.
彼佳Ransomware
类似于WannaCry, Petya ransomware typically was deployed with the ability to spread easily 和 quickly locate vulnerabilities. Users would encounter it as a reboot request, after which their systems would become unavailable. Petya was first launched as malicious email attachments that would infect a system after a user clicked on the attachment 和 it downloaded locally.
最初的Petya袭击在乌克兰各地造成了大规模破坏, severely affecting its banking infrastructure as well as other critical sectors in the country. 从那里,它像野火一样蔓延到整个欧洲. 随后的变体, 被称为NotPetya, featured even more malicious capabilities than the original version 和 also caused billions of dollars in damage.
CryptoLocker Ransomware
也许是这些例子中最持久的, CryptoLocker主要通过包含恶意附件的网络钓鱼电子邮件引诱受害者. 这也许是一个好时机,让我们停下来赞美一下 安全意识培训. 并不是所有的, but many of these attacks require an action on the part of the user to be able to access their system(s), 因此,让员工意识到该采取什么行动和不该采取什么行动是很重要的.
值得注意的, CryptoLocker was particularly effective due to bad actors mimicking prompting actions of well-known companies like FedEx 和 UPS. 非对称加密用于锁定用户的文件, 这意味着使用两个密钥:一个用于加密,一个用于解密.
如何预防勒索软件
Ransomware can be prevented by following key best-practice behaviors that should flow throughout the whole of any security program. 放大, there are two key phases of a ransomware attack during which action is critical in order to lower risk 和 prevent the worst effects of an attack.
- 袭击发生前最小化 攻击表面 通过识别攻击者用来部署勒索软件的特定技术. 从那里, security teams can 应用 layers of preventative measures – this includes workforce training – 和 reduce risk. Purposeful network segmentation can ensure critical machines are isolated to prevent the spread of 恶意软件.
- 攻击期间对于正在进行的攻击,应该严格限制对关键任务数据的访问. Constant system backup should be a high priority so that — in the event mission-critical data is compromised — data restores can be deployed using recent, 不妥协的备份.
Avoid becoming a repeat victim by identifying 和 remediating the initial access 和 execution vectors in the first attack to ensure complete attacker eradication.
如何移除勒索软件?
勒索软件可以通过有效的反恶意软件解决方案扫描网络来清除. Teams should be able to automatically investigate 和 contain ransomware/恶意软件 before it can do real damage.
扫描发现后, it’s a good idea to quickly remove a targeted user’s domain account from the local administrator group. User accounts with administrator rights allow for automated 和 targeted attacks to interact with system-level privileges 和 easy deployment of ransomware.
另外, system administrators can generate decision points for security analysts to block infected user accounts 和 恶意软件 communications – or completely quarantine machines from the network. 利用自动化来减缓感染, 安全响应人员将有更多的时间来完全消除勒索软件的威胁.